SPECIAL ISSUE: Printing with Privacy on Bambu
Flashforge shows the danger of printers without privacy. Here's how to configure your Bambu to ensure your printer can't tattle on you.
TL;DR: here’s how to configure your Bambu to ensure it can’t spy / tattle on you:
To learn more about how to do each of these things, keep reading!
You can also view a condensed version of this post in video form:
Intro: Flashforge Steps on a Rake
If you haven’t seen already, Flashforge put out an announcement yesterday claiming that they prohibit the manufacture of certain kinds of parts on their printers, and threatening “account termination and referral to authorities” for anyone who violates this policy.
Of course, they got completely destroyed in the comments. They’ve since deleted the post and are trying to walk back the threats:
Clearly the outrage was effective in some sense (I’ve written more about this here), but what’s more interesting to me is their technological claims. Can Flashforge actually prohibit you from printing 3D2A parts?
I’ve never actually used a Flashforge printer, but based on a quick review, it looks like the answer is - kind of.
Flashforge uses a proprietary slicer, and their firmware is closed source, meaning that they could put code in either of these to tattle on you if you try to print something spicy.
That said, I’m not really concerned, because Flashforge just doesn’t seem to have that big of a following in the 3D2A community. But there’s another printer that is very widely used, for which people have a similar concern: Bambu printers.
Regarding Bambu Printers
Bambu printers are very popular in 3D2A. This is because Bambu printers essentially work right out of the box, producing super high quality prints in many different materials, including nylons.
Unlike my old Ender or Prusa, I have never had to spend time trying to tune my Bambu - it just works. They’re fantastic printers for people who want to focus on 3D2A, not on tinkering with the printer itself.
This said, a lot of people have concerns that Bambu could do the same thing Flashforge is trying to do.
Bambu has never put out any similar kind of anti-3D2A announcement, and they actually seem to tolerate 3D2A pretty well. But because certain parts of their software are also closed source, we can’t know for certain whether they’re monitoring our prints.
Does this mean we have to forego these fantastic printers out of privacy concerns?
No, we don’t. I’m going to show you how you can set up your Bambu printer so that you can fully maintain your privacy and not worry about printing whatever you want.
It’s actually really easy if you follow three basic rules.
Configuring your Bambu for Privacy
To start with, let’s review the three ways a 3D printer could tattle on you for printing something spicy:
1. The slicing software could detect you are slicing a certain kind of part
2. The upload functionality could report on what you are trying to upload
3. The printer itself could detect and stop you from trying to print a spicy file
For all three of these items, you can configure your Bambu to make it impossible for them to monitor or block what you’re doing.
Starting with the slicing software. Bambu’s first-party slicing software is Bambu Studio, which is actually partially open source.
Certain parts, namely the networking plugin, are closed source (we’ll get to that later) but the core slicing software appears to be open. This means that anyone can read the code, and any functionality added to detect and tattle on you for slicing 3D2A files could be found.
This is good, but if you really want to be safe, you can instead use a different third party slicer called OrcaSlicer.
OrcaSlicer is fully open source, and functions almost identically to BambuStudio, but Bambu (the company) has no control over it, meaning they can’t introduce any monitoring code.
So, the first rule to print privately on Bambu is: use OrcaSlicer to slice your prints.
Don’t Use Bambu’s Cloud Service
Now let’s talk about uploading sliced prints to your printer.
This is where people have the biggest concerns, because Bambu’s marketing and documentation tries to point you towards uploading your sliced files via their cloud service to your printer.
This means that your print data travels all the way to Bambu’s servers before being sent back to your printer. Who knows what they’re doing with that data?
Fortunately, you can avoid this entirely by simply not uploading your prints through the cloud service, and instead transferring them via micro SD card, just like on an Ender printer.
For some reason I don’t think many people know you can do this, but it’s actually very easy to do.
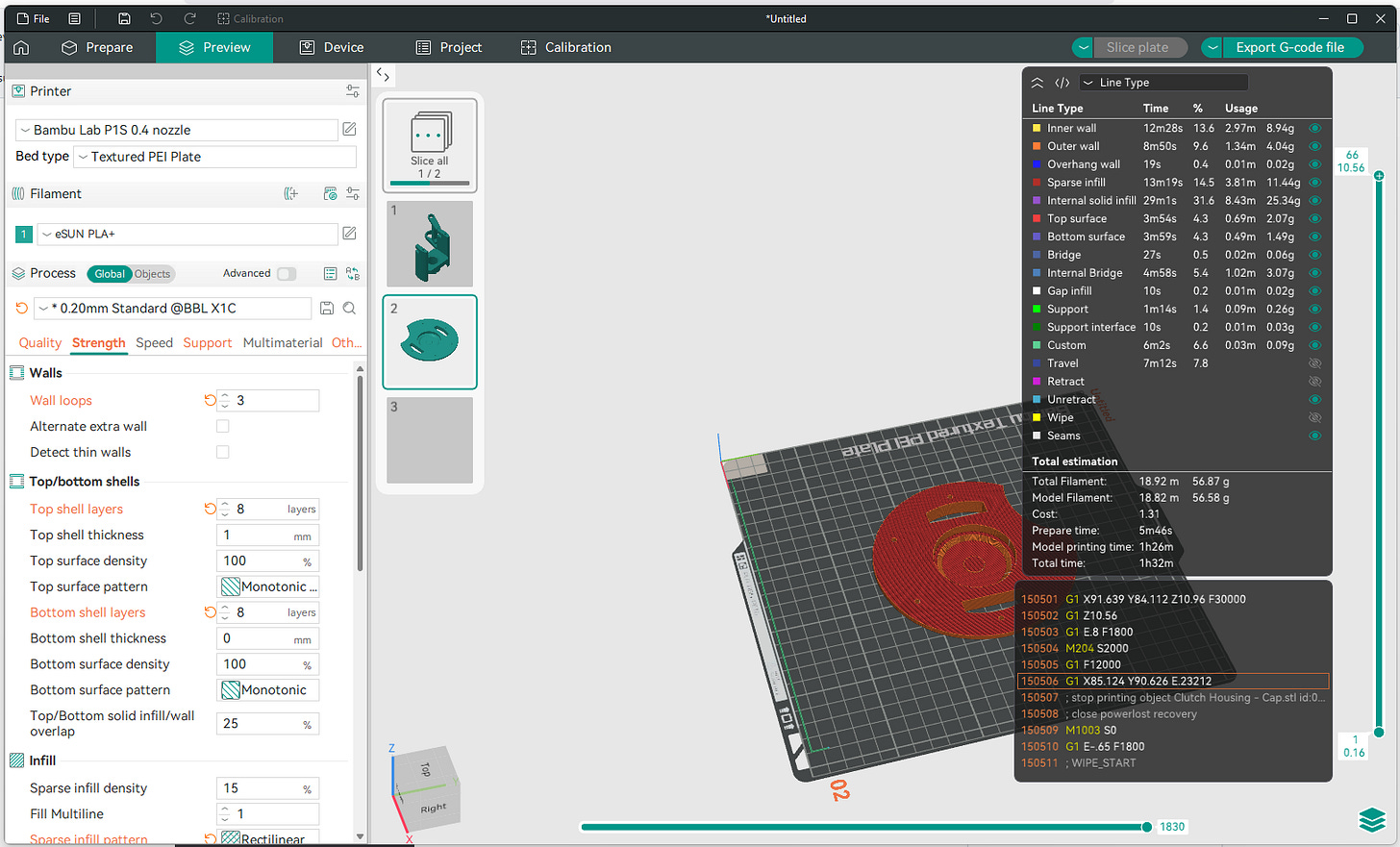
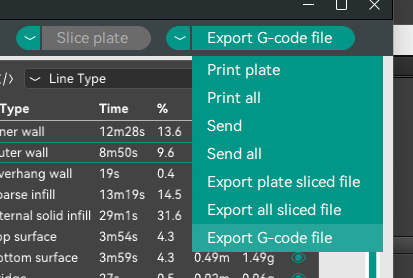
All you have to do is plug your printer’s micro SD card into your computer, and then after slicing in OrcaSlicer, choose “Export G-Code file”.
Write the gcode file to the “model” folder in your SD card.
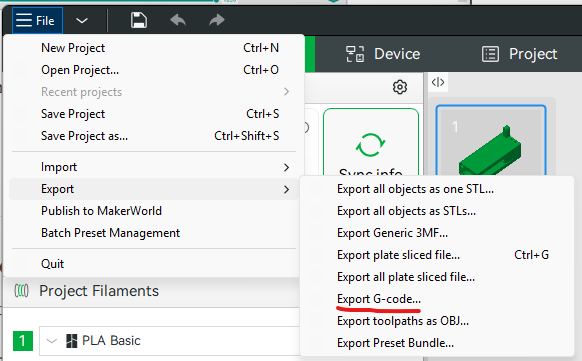
You can also do this in Bambu Studio, although it’s a little hidden - go to File > Export > Export Gcode.
Once the file is exported, plug the micro SD card back into your printer, and now you can select and print the sliced file on your Bambu printer’s control panel.
Uploading this way means that your gcode never travels over any networks, so it can’t be monitored.
As such, the second rule to print privately on Bambu is: only upload sliced prints via exporting the gcode to your micro SD card.
Sidebar: LAN Mode (Don’t Bother)
TL;DR: the conclusion is to not bother with LAN mode, so you can skip this section unless you really care about printer software politics.
By the way, I am aware that Bambu also offers LAN mode, where you can upload your files wirelessly over your local network without sending them through the Bambu cloud.
This is a little complicated. It’s first worth noting that while LAN mode may be usable via Bambu Studio, at time of writing it is not usable with OrcaSlicer.
Bambu attempted to block third party software from accessing network functionality (either the cloud service or LAN mode) in January 2025, causing significant outrage.
In response to the outrage, Bambu attempted to make concessions that would still allow OrcaSlicer (and other third party software) to upload sliced files wirelessly. Yet OrcaSlicer rejected these concessions, and it appears that, at time of writing, this remains the current state of play.
To me, this is all academic, because even if LAN mode worked with OrcaSlicer, I wouldn’t bother with it. Our goal is to ensure our workflow is private, and nothing is more private than direct transfer via micro SD card.
As such, I haven’t attempted to configure LAN mode with either OrcaSlicer or Bambu Slicer, and I recommend you similarly ignore it. Just use the micro SD card.
Keep Your Printer Off the Network
Finally, let’s talk about the printer itself. Bambu’s firmware (the software running on the actual printer hardware, responsible for controlling the printer’s movement) is totally closed source.
As such, some people suggest that this firmware could be configured to detect that you’re trying to print a 3D2A part, could block your print, and could even report you back to Bambu (or the feds!)
I think this is technically dubious. But because the firmware is closed source, we can’t be certain that Bambu isn’t trying to do this.
The good news is that, even if they were, we can defeat it entirely by simply not connecting your Bambu printer to the internet.
When you first set up the printer, Bambu asks you to connect the printer to your local wifi, and it asks you to register the printer on their app. But there’s nothing stopping you from simply ignoring / skipping these requests.
You do need to register if you want to use the cloud upload service, but we’re not using that, so we can simply run our printer in autistic mode. No matter what it tries to do, it can never communicate with the outside world, and your privacy is secured.
(Note: I’ve encountered several reports saying that you can’t skip connecting to the wifi or connecting to the app, and yet I was able to easily do so myself in my own testing. I think the context of these reports is people trying to use the wireless upload functionality. If you eschew that entirely and use only micro SD, then there’s no technical reason you need to connect to the network.)
If you’ve already got your printer set up, you can do a factory reset on it to remove any stored pairings or wireless credentials, and if you really want to be certain, you can change your wifi password so it can’t secretly still connect.
Sidebar: Regarding 3D Gun’t
TL;DR: the conclusion is that you don’t need to worry about sinister secret firmware that will block you from printing a gun. If you want to read why I think this, read on - otherwise, you can skip this section.
The above section focuses on blocking the firmware’s ability to “phone home” - to report on what you are printing.
But what if the firmware contains functionality to detect and block you from printing guns without needing to phone home? This is the premise of 3D Gun’t, software which claims to, when added to a printer’s firmware, identify and stop you from printing gun parts.
The above article claims that the 3D Gun’t firmware is already in place on certain “key printer manufacturers”. Scary stuff!
Here’s the thing: I have never seen a single report on someone being blocked in the way 3D Gun’t describes. This is the kind of thing that would go viral if it happened, so the fact that I’ve seen no reports is somewhat telling.
I also find the claim that such functionality could be entirely embedded within a printer’s firmware to be implausible.
Serious 3D gun detection software (i.e. something that couldn’t be trivially defeated) would necessarily be large and complex. Bambus aren’t running powerful computers onboard - they’re running low-cost, low-power microcontrollers, not suited for performing the kind of analysis 3D Gun’t claims to do.
The normal way to build such a thing would be to have the firmware contact a remote server to do the hard, computationally complex work of detecting a 3D gun print. As such, isolating the printer from the network would prevent the analysis from working.
Even if the Bambu hardware could realistically perform this work locally, the analysis would likely require a large database of reference data. Such a database would need to be regularly refreshed to avoid becoming obsolete.
Once again, refreshing the database would require a network connection. No network connection means a database that quickly goes out of date.
These observations, taken in sum, indicate to me that 3D Gun’t is primarily a publicity stunt, meant to influence the narrative around 3D printed guns. I’m not saying the software is totally fake, but instead that whatever does exist is meant to function primarily through creating dispiriting narratives, vs. effectively functioning on a technical level.
(We have seen such things before - old guncad hands may recall the French company Dagoma, which claimed to be releasing intentionally nonfunctional 3D guns onto the internet, in an attempt to “poison” 3D gun repositories. This created lots of consternation, but to my knowledge no “poisoned” files were ever actually found.)
If anyone does know of credible reports of a printer blocking someone from printing a gun, please let me know. Otherwise, I think the right move is to treat 3D Gun’t and similar projects as psyops, meant primarily to demoralize the 3D2A community.
Conclusion
So that’s all there is to it. With these really basic steps, you can ensure that it’s technologically impossible for Bambu to spy on you, and you can use these fantastic printers without compromising your privacy. Again, the three rules are:
Use OrcaSlicer instead of BambuStudio
Only upload your prints via the micro SD card, never with the cloud upload service
Never connect your Bambu printer to the wifi or register it on the Bambu Handy app.
I hope this writeup makes people feel better about using Bambu printers.
If you have been holding off on getting a Bambu because of these concerns, I have good news - you can now buy Bambus at 3D Print Freedom!
I’ve been using Bambu printers for years now, as have a significant number of other 3D2A developers and hobbyists. I genuinely believe these printers are the best way for someone to get into the hobby, and I believe that, if you follow the advice above, you can feel confident that your privacy will remain secure.
Thank you for reading this special issue of the Guncad Digest! If you want future issues delivered straight to your inbox, you can subscribe to this Substack.
You can also follow us on Twitter, Instagram, Facebook, or Reddit, where we’ll post notifications when a new issue of the Digest is live!







The comments section below ended up being a rather nice illustration of precisely the thing I'm warning about with taking propaganda at face value.
DJ is making claims below about finding "50+ files" that are "incorrect and changed", "key features left out", "warped", etc. He uses this as proof of someone intentionally going in and messing with files. When asked to provide proof he clams up a bit and only wants to talk over "secure channels".
The key points to this narrative are:
1. A massive number of files are messed up
2. This includes even popular files by established devs, like the Not-A-Glock
3. This "file poisoning" is being done intentionally by nefarious forces
As with a lot of the claims I discuss in my original post, this narrative is neither technologically or sociologically plausible.
1. It's not technically plausible because there is no known method for a nefarious actor to "poison" somebody else's Odysee release, e.g. the Not-A-Glock. To be clear, this would mean hacking Odysee and modifying someone's claim. Everything about Odysee's blockchain architecture is meant to forestall this sort of thing.
2. It's not sociologically plausible because, if this poisoning was happening at this scale, it would be detected and broadly discussed on the many established 3D2A platforms (/r/3D2A, Guncad Index forums, Rocketchat, etc.) - not in the comments section of a random Substack post.
Shittinator has suggested that DJ is intentionally spreading misinformation (https://x.com/theshittinator/status/1990529154304156005). Maybe - but I prefer to first think that DJ is someone who, like lots of people, isn't super technically knowledgeable, and is partial to scary-sounding narratives.
It's easy to imagine DJ opening up a few files and seeing details / qualities that look wrong to him, or printing a file and finding that his print is out of spec. He's also heard about some nefarious group putting out bad files. It's fun and interesting to jump to the conclusion that his bad print is due to an intentionally poisoned file, and that this must be happening at a grand scale.
Of course, in the absence of further evidence, I find it much more likely that his printer is just not tuned well (should have got a Bambu :)
People like to draft and share conspiracies. It's fun. But it's a problem when, in an article that tries to help new gun printers feel comfortable printing a file safely and privately, the first thing they see in the comments section is an unproven conspiracy. DJ may or may not be intentionally spreading FUD, but even if it's not intentional, *the effect is still the same.*
This is the danger of accepting psyops at face value. The purpose of the Dagoma "file poisoning" project was almost certainly not to actually put bad files out there, *but to get people to forever worry about bad files.*
The result is that, when someone like DJ's prints don't work, their reaction is not to learn more and become better printers / gun builders, but to chalk it up to a conspiracy. And why bother growing and improving if the feds are just going to fuck you over regardless?
As a community we must learn to be realistic about our vulnerabilities and attack surfaces. We must learn when vigilance is appropriate, and when it mutates into paranoia. And we must stop spreading fear and doubt that scares new people off.
Help new people recognize the legitimate hazards and risks of gun printing, certainly - but never let this mutate into unfounded fearmongering.
Sent you and email Alyosha. Please keep my info anynommous. Thanks